- Joined
- Sep 25, 2012
- Messages
- 10
- Reaction score
- 2
I manage several instances of 3CX, and I constantly see tons of authentication failures from scans, what I currently do is manually add the IP's from the several installations into a global blacklist. But the issue is, I cannot reuse that information, nor could others.
So my suggestion is to add support for dnsbl, meaning every connect from non-reserved ip space would be checked against <reverseip>.<listname> through dns, if that request returns a reply in the 127.0.0.0/8 range, it would deny the connection attempt. (See RFC5782)
Another suggestion for Blacklist would be the ability to export the data.
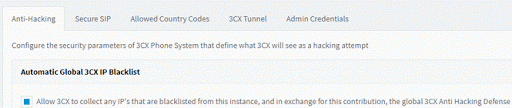
To complete the blacklist enhancements I have in mind, perhaps 3CX itself wants to run a dnsbl, giving users the ability to optionally submit detected hack attempts to 3CX, if multiple instances report the same ip as bad (score based in order to prevent abuse of the system), other connected instances would also block attempts from these IP's.
So my suggestion is to add support for dnsbl, meaning every connect from non-reserved ip space would be checked against <reverseip>.<listname> through dns, if that request returns a reply in the 127.0.0.0/8 range, it would deny the connection attempt. (See RFC5782)
Another suggestion for Blacklist would be the ability to export the data.
To complete the blacklist enhancements I have in mind, perhaps 3CX itself wants to run a dnsbl, giving users the ability to optionally submit detected hack attempts to 3CX, if multiple instances report the same ip as bad (score based in order to prevent abuse of the system), other connected instances would also block attempts from these IP's.
Upvote
2